In light of the recent CVE-2024-3094 incident, which underscored the sophisticated vulnerabilities in widely used tools like XZ Utils, it’s imperative for CIOs and CISOs to reassess their cybersecurity strategies. The incident not only revealed the potential for significant breaches across sectors but also highlighted the complexities of managing and monitoring a comprehensive digital asset portfolio. This context brings to light the necessity for advanced cybersecurity solutions capable of navigating the evolving threat landscape.
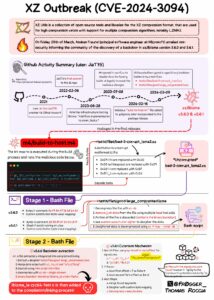
XZ Outbreak (CVE-2024-3094) summary by Thomas Roccia (@frogger) – source
The CVE-2024-3094 Incident Overview
The CVE-2024-3094 vulnerability within XZ Utils posed a stark reminder of the challenges in securing open-source software components—a staple in many organizational IT environments. Attackers exploited this vulnerability to potentially infiltrate systems across various sectors, leveraging sophisticated techniques like multi-stage obfuscation and encrypted payloads.
The discovery of CVE-2024-3094 within the XZ Utils compression tool has profound implications for cybersecurity strategies, especially in organizations heavily reliant on Linux environments and open-source software. This backdoor vulnerability exposes critical weaknesses not only in software supply chains but also in the overarching approach to digital asset management and security monitoring
The CVE-2024-3094 vulnerability was embedded through sophisticated multi-stage obfuscation and encryption techniques, making detection particularly challenging. The backdoor was designed to execute malicious payloads discreetly, exploiting the trust in the XZ Utils’ widespread adoption across various Linux distributions. This vulnerability serves as an entry point for attackers to potentially gain unauthorized access to systems, highlighting the need for robust monitoring of both internal and external digital assets. The ability for such a backdoor to remain undetected underscores the sophistication of modern cyber threats and the necessity for advanced detection capabilities.
Implications for Cybersecurity Asset Management
The incident illustrates the critical need for dynamic asset visibility and control. Organizations must have a comprehensive understanding of their digital asset landscape, including internal and external components. This not only aids in identifying potential vulnerabilities but also in prioritizing security efforts based on the risk profile of each asset.
The incident brings to light vulnerabilities in the software supply chain, emphasizing the importance of scrutinizing third-party components and dependencies. CIOs and CISOs should consider adopting comprehensive security measures that include vetting open-source software for potential backdoors or vulnerabilities, implementing secure coding practices, and ensuring regular updates and patches are applied.
Effective cybersecurity asset management should encompass a real-time inventory and monitoring of all digital assets. Organizations need to deploy solutions that can dynamically identify and assess the security posture of both hardware and software assets, applying contextual intelligence to prioritize risk and response strategies.
The evasion techniques used in CVE-2024-3094 advocate for the adoption of proactive threat detection mechanisms. Leveraging advanced analytics, artificial intelligence, and machine learning can help in predicting potential vulnerabilities and threats, enabling preemptive remediation actions.
Streamlined Compliance and Risk Management
The broad implications of CVE-2024-3094 on compliance and risk management highlight the need for continuous compliance monitoring and risk assessment frameworks. Automating compliance processes and integrating them with ongoing risk management efforts can ensure that organizations remain compliant with relevant regulations and standards while effectively managing cybersecurity risks.
The adaptability of cybersecurity strategies is paramount. Tools and solutions like XRATOR Operator and XRATOR AutoComply that offer customizable security assessments enable organizations to align their cybersecurity measures with specific operational needs and emerging threat vectors, ensuring that defenses remain robust in the face of novel challenges.
The Role of Collaborative Cybersecurity Ecosystems
The CVE-2024-3094 incident also highlights the value of collaboration within the cybersecurity community. Sharing threat intelligence and leveraging collective knowledge can enhance an organization’s defensive strategies, providing a more comprehensive shield against cyber threats.
Lastly, the CVE-2024-3094 incident illustrates the value of collaboration within the cybersecurity community. Sharing insights, threat intelligence, and mitigation strategies can enhance an organization’s defensive posture. Engaging in cybersecurity consortia and platforms for intelligence sharing can provide early warnings and collective insights into emerging threats and vulnerabilities.
Conclusion
The CVE-2024-3094 incident serves as a critical wakeup call for CIOs and CISOs to evaluate and enhance their cybersecurity frameworks. In an era where cyber threats are increasingly sophisticated, leveraging advanced cybersecurity solutions that offer a holistic view of the organization’s digital assets, coupled with proactive threat detection and adaptable risk management strategies, is essential. Embracing a collaborative approach to cybersecurity can further strengthen defenses, ensuring organizations can navigate the complexities of the digital age with confidence.






