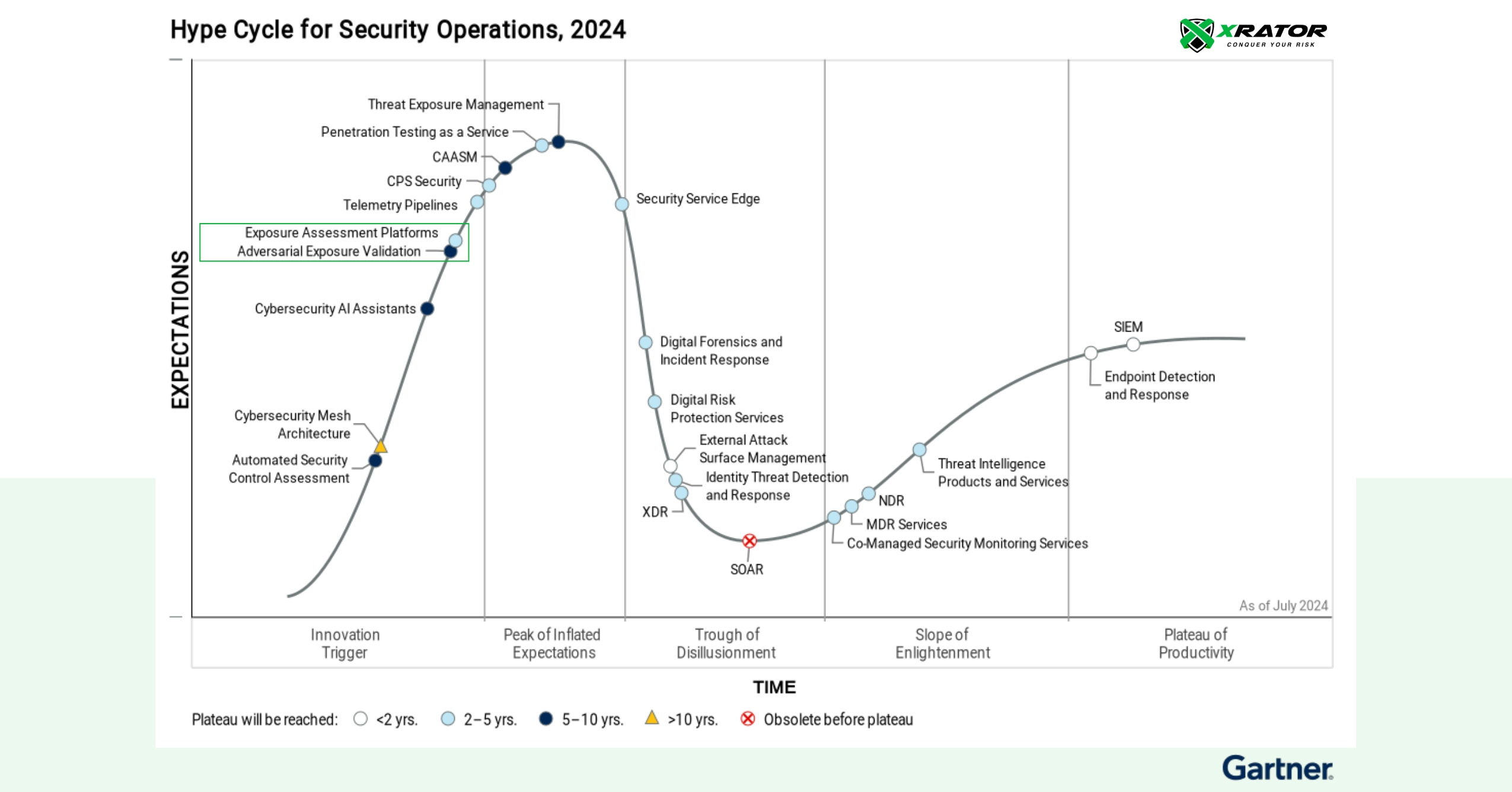
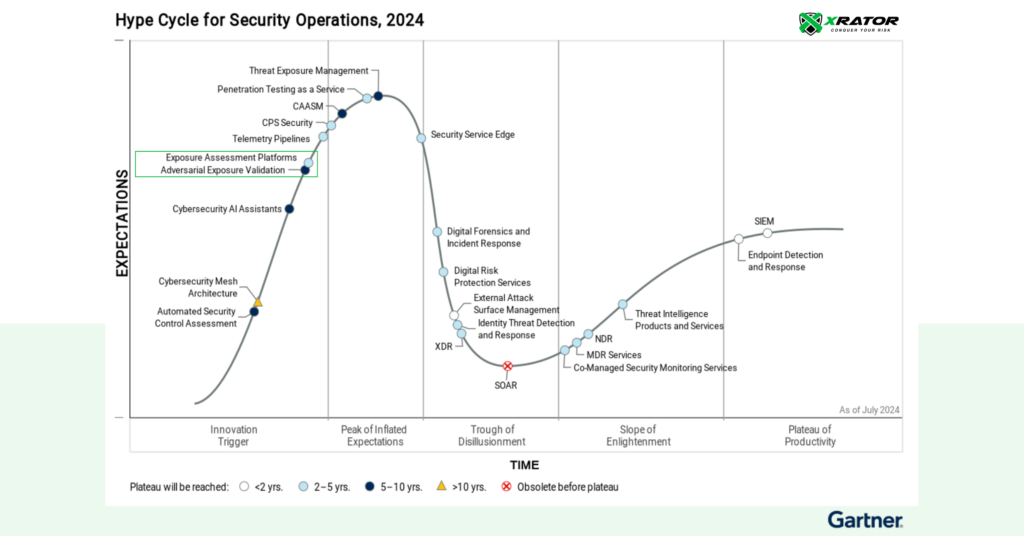
Organizations are increasingly recognizing the need for robust solutions that go beyond traditional vulnerability management. Two emerging categories—Exposure Assessment Platforms (EAPs) and Adversarial Exposure Validation (AEV)—are gaining prominence as highlighted in Gartner’s 2024 Security Operations Hype Cycle. These technologies reflect evolving approaches to continuous threat exposure management (CTEM), a framework designed to improve how organizations govern and operationalize their exposure management processes.
EAPs and AEVs serve complementary roles within the CTEM framework: EAPs consolidate vulnerability assessment and prioritization technologies, offering end-users simplicity and effectiveness in managing attack surfaces, while AEVs validate the exploitability of vulnerabilities and the effectiveness of security controls. Together, they provide organizations with a more complete view of their security posture, enabling proactive, strategic risk management.
This article will delve into the distinctions between these two approaches, spotlighting key players like XRATOR and Pentera, and exploring how these innovations are reshaping the way businesses address their exposure management challenges.
Understanding Exposure Assessment Platforms (EAPs)
Exposure Assessment Platforms are designed to identify, assess, and prioritize security exposures across the whole organization’s digital assets. Companies like XRATOR, Balbix, and Armis exemplify the capabilities of EAPs, which include:
– Continuous Monitoring: EAPs provide ongoing visibility into vulnerabilities and misconfigurations within an organization’s IT infrastructure.
– Contextual Risk Assessment: They leverage contextual data such as business criticality and threat intelligence to prioritize vulnerabilities based on their potential business impact.
– Integration with Existing Security Tools: EAPs can integrate with other security solutions to enhance operational efficiency and streamline vulnerability prioritization processes.
For instance, XRATOR stands out with its advanced analytics and user-friendly interface, enabling organizations to quickly identify high-risk vulnerabilities, severe asset’s exposure and implement effective remediation quick wins.
The Role of Adversarial Exposure Validation (AEV)
On the other hand, Adversarial Exposure Validation focuses on simulating real-world attack scenarios to validate the effectiveness of security controls or the exploitability of a vulnerability. Key players in this domain include Pentera and XMCyber. AEV provides:
– Real-World Attack Simulations: By mimicking the techniques of cyber adversaries, AEV tools reveal vulnerabilities that are indeed exploitable by cyber adversaries.
– Automated Penetration Testing: This reduces the need for specialized skills in red teaming or penetration testing by automating some aspects of the testing process.
– Continuous Validation of Security Posture: AEV helps organizations understand how far an attacker could potentially penetrate their defenses.
Pentera’s platform exemplifies this approach by offering targeted simulations that challenge an organization’s defenses, providing insights into security gaps.
When Organizations Need Both EAPs and AEV
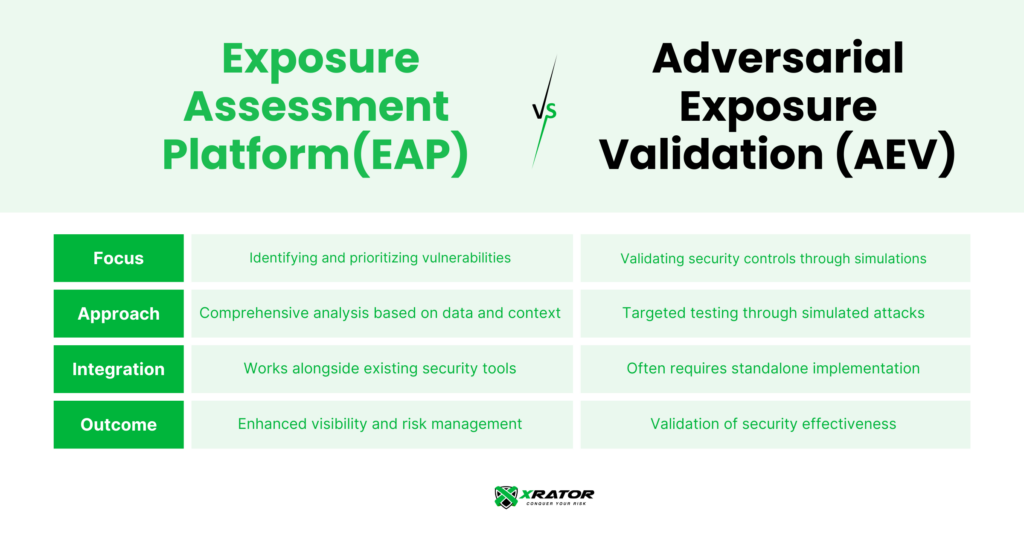
Integrating both Exposure Assessment Platforms (EAPs) and Adversarial Exposure Validation (AEV) into a cybersecurity strategy provides organizations with a comprehensive approach to risk management. Each serves a distinct yet complementary purpose: EAPs, like XRATOR, offer deep insights into potential vulnerabilities, while AEV platforms, such as Pentera, validate whether those vulnerabilities can be exploited in real-world scenarios. Together, they form a robust framework for continuous threat exposure management.
An effective AEV strategy relies on a well-implemented EAP as its foundation. EAPs provide a comprehensive, prioritized assessment of vulnerabilities, enabling organizations to focus their efforts where it matters most. These prioritized vulnerabilities can then be passed to the AEV, which further evaluates and validates the critical ones to determine their exploitability.
Without a proper EAP, running an AEV becomes counterproductive. Organizations risk validating the exploitability of vulnerabilities or testing the robustness of security controls in areas that may be irrelevant from both a business and threat perspective. By starting with EAP and then incorporating AEV, organizations ensure their efforts align with real-world risks and deliver meaningful results.
The Future of Cybersecurity with XRATOR
As organizations increasingly adopt a proactive stance towards cybersecurity, platforms like XRATOR are at the forefront of this evolution. By combining advanced exposure assessment capabilities with seamless integration into existing workflows, XRATOR empowers organizations to identify and prioritize risks treatments based on their potential impact on business operations.
Conclusion
The landscape of cybersecurity is shifting towards continuous threat exposure management, that combines exposure assessment with adversarial validation. As organizations navigate this complex environment, leveraging both EAPs and AEV will be crucial for maintaining a strong security posture. With platforms like XRATOR leading the way in exposure assessment and companies like Pentera excelling in adversarial validation, businesses can effectively safeguard their digital assets against evolving threats.
By understanding the differences between Exposure Assessment Platforms vs. Adversarial Exposure Validation, organizations can make informed decisions about their cybersecurity investments, ultimately enhancing their preventive cyber capabilities.