The recent IBM and Palo Alto Networks study on security platformization makes a compelling case: consolidating security tools delivers measurable operational benefits. With organizations juggling an average of 83 different security solutions from 29 vendors, the integration imperative is clear. The financial argument—platformized organizations seeing 101% ROI versus just 28% for non-adopters—is difficult to ignore.
The IBM/Palo Alto study brings an interesting perspective on cybersecurity platformization but fail to explain how to go from technical consolidation to strategic translation.
Ronan Mouchoux – CTO @XRATOR
Yet beneath these impressive figures lies a more profound truth that technology leaders must recognize: cybersecurity platformization alone is an insufficient strategy for true cyber resilience.
The Metrics-to-Meaning Gap
The fundamental limitation in current security platformization thinking is a persistent disconnect between technical security indicators and business outcomes. IBM’s research confirms that 96% of security executives who have adopted platformization view security as a source of value—but what exactly constitutes “value” remains ambiguous in most security architectures.
This ambiguity persists because we’ve been asking the wrong question. The critical question isn’t “How do we consolidate our security technologies?” but rather “How do we translate security intelligence into strategic business insight?“
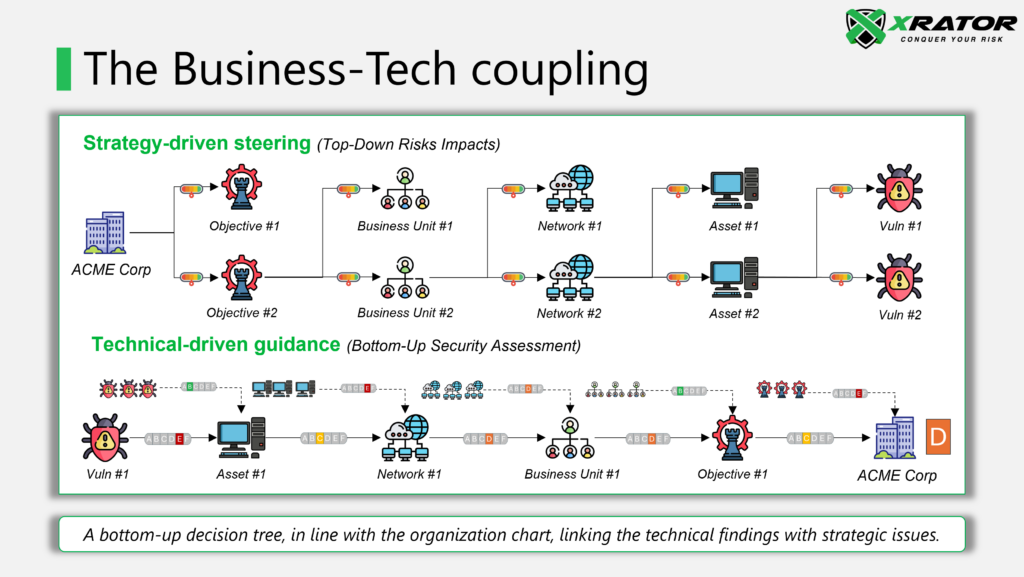
The Translation Imperative
A truly mature security approach requires not just technical consolidation but strategic translation—turning security metrics into business meaning. This represents the next evolution in security architecture, moving beyond security platformization to what I call “business-centric security architecture.“
The distinction is important:
- Security Platformization focuses on integrating technical capabilities, reducing tool sprawl, and enhancing operational efficiency.
- Business-centric security architecture starts with organizational priorities and builds a translation layer that connects technical indicators to strategic outcomes, risk scenarios, regulatory standing, and operational continuity.
This translation capability requires security leaders to develop what has historically been their weakest skill: the ability to render complex technical situations into clear business implications that executives can immediately grasp and act upon.
From Technical Debt to Strategic Asset
When security is established as a business-driven function rather than a technology-driven one, the entire conversation changes. Security ceases to be measured by the number of vulnerabilities patched or incidents detected and instead becomes evaluated by its contribution to business resilience, market expansion, and competitive differentiation.
Consider the difference:
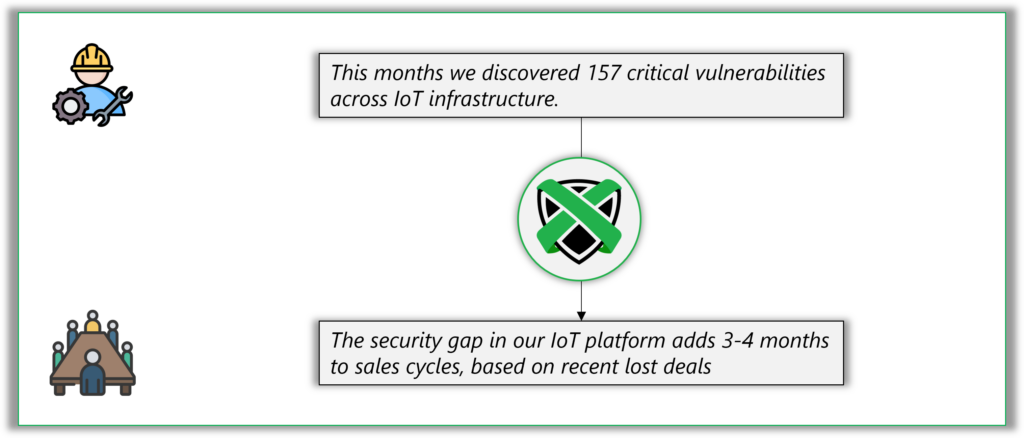
- A traditional security report might highlight “157 critical findings across IoT infrastructure“
- A business-centric security architecture would translate this into “The security gap in our IoT platform adds 3-4 months to sales cycles, based on recent lost deals“
This translation allows executives to make informed trade-off decisions, balancing security investments against tangible business outcomes rather than abstract technical improvements.
Building the Translation Layer
Creating this translation capability requires three foundational elements:
1. Business Risk Contextualization
Each security event, vulnerability, and compliance control must be mapped to specific business risk scenarios. This mapping process should be systematic, repeatable, and adaptive to changing business conditions.
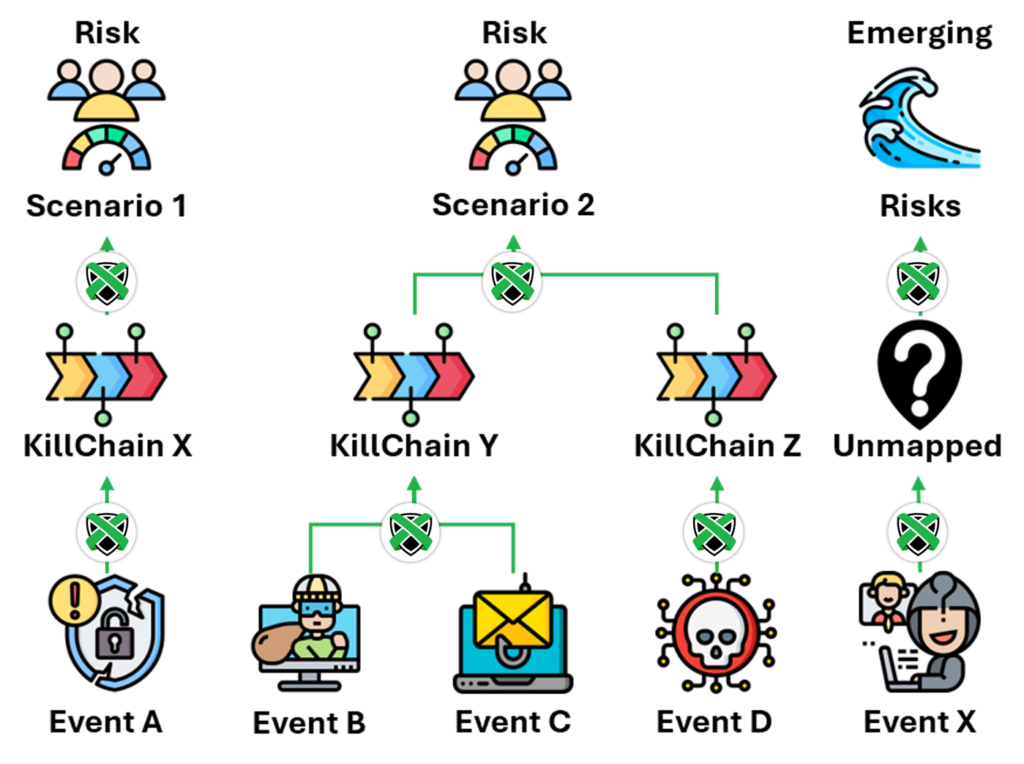
Rather than presenting raw technical data, security leaders must develop models that demonstrate how each technical vulnerability impacts business operations, from customer experience to supply chain resilience to market expansion capabilities.
2. Granular Business Impact Scoring
Traditional severity scoring (like CVSS) provides insufficient business context. Organizations need multi-dimensional scoring systems that factor in:
- Business criticality of affected systems
- Strategic importance of impacted capabilities
- Financial implications of potential compromise
- Regulatory and compliance consequences
- Operational disruption scenarios
This more nuanced approach allows for precise prioritization based on business impact rather than technical severity alone.
3. Continuous Strategic Alignment
The most sophisticated security architectures establish feedback loops between security operations and strategic business initiatives. Each security finding becomes an opportunity to refine the organization’s risk models, and each business initiative informs the evolution of security priorities.
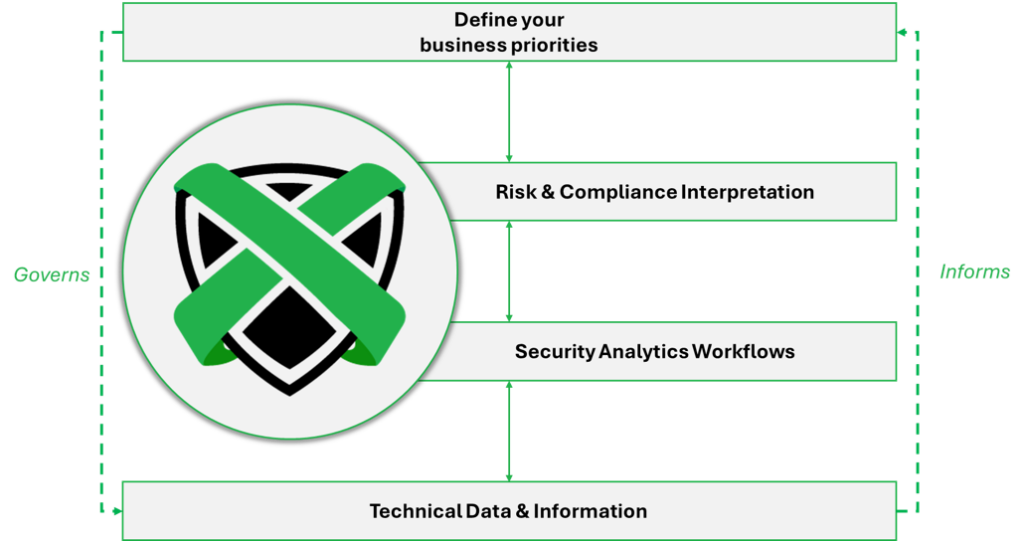
This bidirectional flow ensures that security becomes embedded in strategic planning rather than merely reacting to technical threats.
The Economic Imperative
Beyond operational benefits, this translation-focused approach delivers substantial economic advantages. When examining real-world implementations of business-centric security architectures, we consistently observe:
- Reduced remediation costs through more precise prioritization
- Accelerated sales cycles where security becomes a market differentiator
- More efficient capital allocation based on business risk alignment
- Enhanced regulatory relationships due to more strategic compliance approaches
- Higher retention of security talent who see the business impact of their work
Our case study of HIRECORP (anonymized) demonstrates this economic impact clearly. After implementing a business-centric security platform, they reduced annual cyber risk management costs from €5,95M to €2,63M while simultaneously improving their security posture—a 55% cost reduction with enhanced protection.
Beyond the Security Platformization
While cybersecurity platformization addresses the urgent need for technical consolidation and operational efficiency, it remains an incomplete solution. The true competitive advantage lies in building the translation layer that connects security intelligence to strategic decision-making.
As regulatory pressures like NIS2, the Cyber Resilience Act, and the AI Act demand board-level security governance, this translation capability becomes not just advantageous but essential. Organizations that develop sophisticated business-centric security architectures will reduce their technical vulnerabilities and transform security from a cost center to a strategic enabler of growth and resilience.
The next frontier in security platformization is not just about better integration of tools, but about better integration of security into the very fabric of business strategy and execution.






