A CISO’s step-by-step Process Translating Technical Security Metrics into Business Value
“What does this mean for our ability to sign new enterprise customers in the Americas?”
The question hung in the air as my carefully crafted presentation on threat intelligence gaps, last quarter penetration testing reports and patch coverage statistics flickered on the boardroom screen of the major AgriTech. The VP Digital Transformation wasn’t being confrontational – she was genuinely asking the one question that actually mattered to their business this year. And I had no answer.
It was nine years ago. I was a young external Information Security Officer specialized in cyber-espionnage prevention.
That moment changed how I think about security metrics forever.
We care about activity, they care about impacts
As security leaders, we’ve built an impressive array of tools to measure our operations. We track mean time to patch, vulnerability density, incident response times, and dozens of other security metrics that help us manage our security programs. These metrics are valuable for running our teams, but they share a fatal flaw: they measure activity, not impact.
When we present these metrics to business leaders, we’re essentially showing them how well our security factory runs without explaining what it produces. It’s like a manufacturing CEO reporting on machine utilization rates without mentioning product quality or revenue.
Not all data is for everyone
This communication gap has real consequences. According to McKinsey, 54% of board members report being dissatisfied with the quality of cybersecurity reporting they receive (Mckinsey Insights). More tellingly, only 43% of businesses and 37% of charity boards discuss cybersecurity at least quarterly—hardly enough to make informed decisions about critical business risks (Cybersecurity longitudinal survey).
The impact goes beyond frustrated executives. When security leaders can’t articulate business value:
- Critical security initiatives struggle to get funding
- Security requirements are seen as obstacles rather than enablers
- The organization takes on unknown risks due to poor understanding
- Security teams become isolated from business units
The process to plug cyber talk into the business governance
The solution isn’t to dumb down our metrics or hide technical details. Instead, we need to reframe security data in terms of business outcomes.
1. Start with Business Context
Before presenting any security metric, ask:
- What business decision will this information support?
- How does this impact revenue, costs, or risk?
- Which strategic initiatives does this enable or protect?
2. Tell Stories, Not Statistics
Instead of reporting “73% patch coverage,” tell the story of how your security program enabled the sales team to close a major deal by meeting the prospect’s compliance requirements.
3. Connect Security to Revenue
Every security metric should trace back to:
- Revenue protection (preventing losses)
- Revenue enablement (supporting sales)
- Cost efficiency (optimizing operations)
- Risk management (protecting market value)
Translating Security for Business Leaders
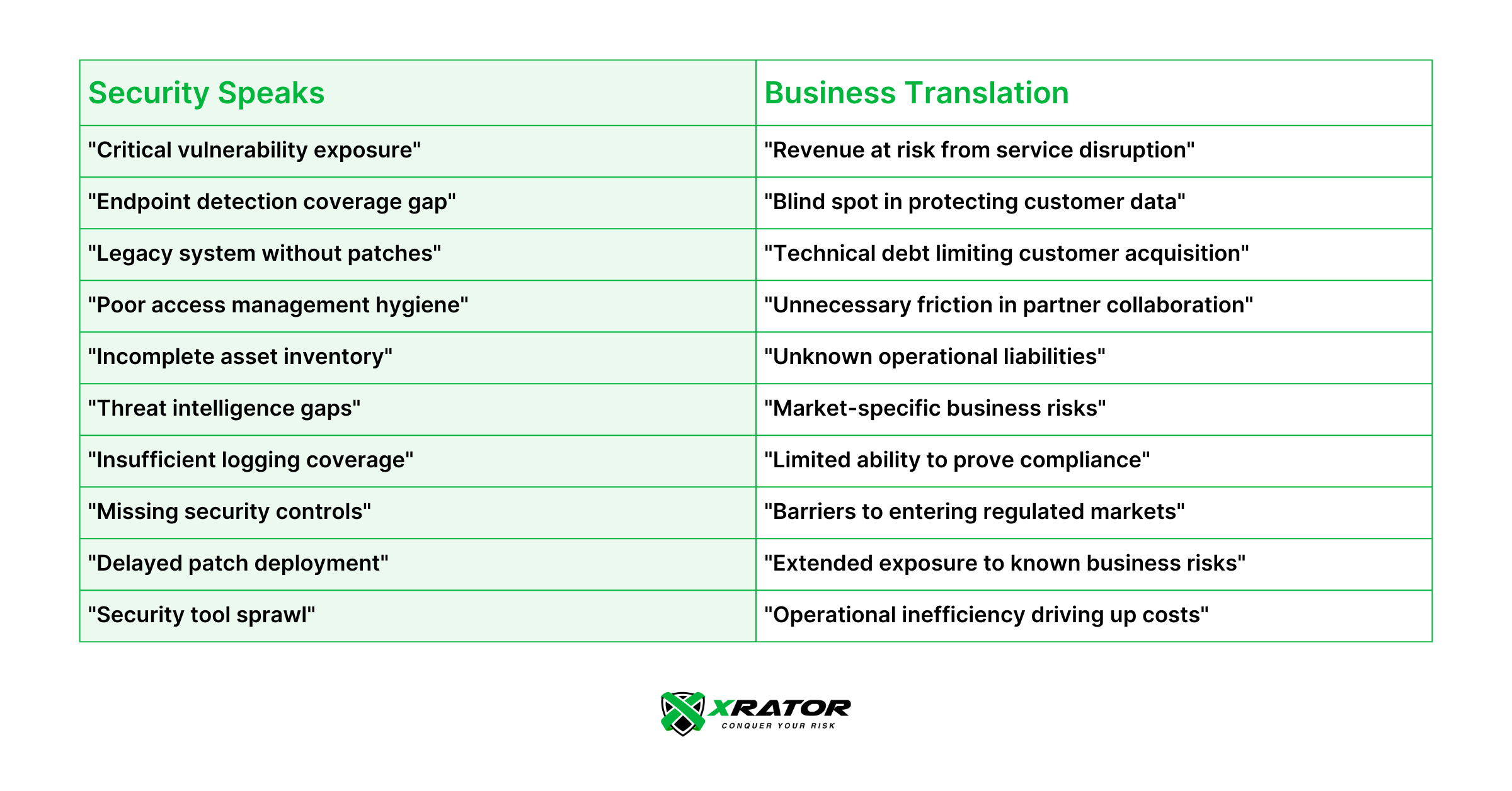
Below is a translation guide for common security concepts into business language:
Practice Ground: Making the Shift in Action
Let’s walk through a realistic scenario that many security leaders face. You’re the CISO of EuroAgri Solutions, a leading European agricultural technology company expanding into the Americas. Your company’s smart farming platforms help large agricultural enterprises optimize their operations through IoT sensors, AI-driven crop management, and supply chain automation.
The Traditional Security Update (Before)
Here’s how many security leaders might typically present their quarterly update:
“Our latest vulnerability scan revealed 157 critical findings across our IoT platform infrastructure, with an average time to patch of 27 days. We’ve improved our patch coverage by 12% compared to last quarter. Our SOC handled 1,243 alerts, with a mean time to respond of 45 minutes. We’ve implemented new EDR tools across 82% of our environment.”
Let’s analyze why this falls short:
- Focuses on operational metrics without business context
- Doesn’t connect to the company’s strategic goals
- Fails to address executive concerns about market expansion
- Leaves the board to interpret security’s impact on sales
Transforming the Message: The Process
Your board has set an aggressive goal: sign 50 enterprise customers in North America over the next 18 months. These prospects include major agricultural cooperatives and food processing companies, many subject to FDA regulations and supply chain security requirements.
Let’s apply our translation framework step by step:
- Start with Business Context
- Strategic Goal: North American market expansion
- Target Customers: Regulated agricultural enterprises
- Timeline: 18-month sales push
- Key Concern: Ability to meet customer security requirements
- Connect Security to Revenue (Using our translation table)
- “Critical vulnerability exposure” → “Revenue at risk from service disruption”
- “Incomplete asset inventory” → “Unknown operational liabilities”
- “Missing security controls” → “Barriers to entering regulated markets”
- Tell a Business Story
- Frame findings in terms of market opportunities
- Focus on enabling sales and reducing friction
- Provide clear, actionable recommendations
The Business-Aligned Update (After)
“Our security analysis has identified three key areas that directly impact our ability to close deals in North America:
First, our current security architecture meets 85% of FDA’s cybersecurity requirements for agricultural supply chain systems. The gap in our IoT platform security controls would require potential customers to obtain special waivers, adding 3-4 months to sales cycles. We’ve developed a 60-day remediation plan that prioritizes the controls most frequently requested during security assessments.
Second, we’ve mapped our security certifications against competitor offerings and identified two specific certifications that would give us a competitive advantage in regulated markets. Based on our analysis of recent lost deals, adding these certifications could reduce prospects drop off by 25% for enterprise customers.
Third, we’ve analyzed security questionnaire responses from our last 20 enterprise prospects. We’ve identified a pattern of concerns around our incident response capabilities. Addressing these would remove a common objection that’s currently extending our due diligence cycle by an average of 45 days, stretching our operationnal efficiency to keep the company safe from cyber attacks.
Our team has developed a 90-day action plan that:
- Prioritizes security investments that directly support revenue generation
- Aligns our security roadmap with marketing & sales team cycles
- Positions us to compete more effectively against key competitors
The total investment needed is €2.1M, with an expected direct return of €18M in accelerated sales pipeline over the next 12 months. We can begin implementation immediately to support next quarter’s sales targets.”
Key Elements That Make This Work:
- Opens with clear business context
- Quantifies impact on sales cycles
- Compares against competitor capabilities
- Provides clear ROI projections
- Offers specific, actionable recommendations
- Ties security directly to revenue generation
This transformed message helps board members understand exactly how security investments support their strategic goals. It moves the conversation from technical security metrics to business outcomes, positioning security as a strategic enabler rather than a cost center.
Moving Forward
Start small. Pick one of the key security metrics and reframe it in terms of business impact. Share it with a trusted business leader and get their feedback. Build from there.
Remember: The goal isn’t to hide technical reality but to connect it to business outcomes. When we bridge this gap, security transforms from a cost center to a business enabler.
Your technical security metrics aren’t worthless – they’re just waiting to be translated into business value.